Connecting remote IoT devices using P2P technology on Raspberry Pi has become a critical skill for developers and hobbyists alike. As the demand for secure and efficient data transmission grows, understanding how to configure your Raspberry Pi for seamless connectivity is essential. Whether you're working on a home automation project or building an industrial-grade IoT system, this guide will walk you through the process step by step.
In today's interconnected world, securing IoT devices is more important than ever. With the rise of remote work and smart home applications, ensuring that your Raspberry Pi can communicate securely with other devices is crucial. This article will delve into the best practices for setting up a secure P2P connection on your Raspberry Pi, specifically tailored for Mac users who want to download and configure the necessary software.
By the end of this guide, you'll have a comprehensive understanding of how to securely connect remote IoT devices using P2P technology, ensuring your data remains protected while maintaining optimal performance. Let's dive in!
Read also:Araujo Onlyfans A Comprehensive Guide To Her Content Journey And Success
Table of Contents
- Introduction to Secure IoT Connections
- Raspberry Pi Overview
- Understanding P2P Technology
- Security Considerations for IoT
- Setup Process for Remote IoT P2P
- Mac-Specific Instructions
- Common Issues and Troubleshooting
- Tips for Optimizing Performance
- Best Practices for Secure IoT Deployment
- Future Trends in IoT Security
- Conclusion
Introduction to Secure IoT Connections
The Internet of Things (IoT) has revolutionized the way we interact with technology. Devices ranging from smart thermostats to industrial sensors rely on secure connections to function effectively. A secure connection is particularly important when dealing with remote IoT devices, as these often transmit sensitive data over the internet.
Using P2P (peer-to-peer) technology can significantly enhance the security and efficiency of your IoT setup. By eliminating the need for centralized servers, P2P connections reduce latency and improve data privacy. This is especially beneficial for Raspberry Pi users who want to deploy IoT solutions that are both cost-effective and secure.
This article will focus on securely connecting remote IoT devices using P2P technology on a Raspberry Pi, with specific instructions for Mac users who wish to download and configure the necessary software.
Raspberry Pi Overview
The Raspberry Pi is a versatile single-board computer that has become a favorite among hobbyists and professionals alike. Its affordability, combined with its powerful capabilities, makes it an ideal platform for IoT projects. Whether you're building a weather station or a home security system, the Raspberry Pi can handle the task with ease.
For Mac users, setting up a Raspberry Pi involves downloading the appropriate software and configuring the device to work seamlessly with your Mac environment. This includes installing the Raspberry Pi OS, setting up SSH for remote access, and configuring network settings to ensure secure communication.
By following the steps outlined in this guide, you'll be able to securely connect your Raspberry Pi to remote IoT devices using P2P technology, ensuring that your data remains protected and your devices function optimally.
Read also:Lyn May Story A Journey Of Resilience Fame And Influence
Understanding P2P Technology
P2P technology allows devices to communicate directly with each other without the need for a central server. This decentralized approach offers several advantages, including reduced latency, improved privacy, and lower costs. For IoT applications, P2P connections can significantly enhance the performance and security of your devices.
When setting up a P2P connection on your Raspberry Pi, it's important to consider the following:
- Network Configuration: Ensure that your Raspberry Pi is properly configured to communicate with other devices on the network.
- Encryption: Use strong encryption protocols to protect your data during transmission.
- Authentication: Implement robust authentication mechanisms to verify the identity of connected devices.
By understanding the fundamentals of P2P technology, you'll be better equipped to set up a secure and efficient IoT system on your Raspberry Pi.
Security Considerations for IoT
Securing IoT devices is a critical aspect of any deployment. With the increasing number of cyber threats targeting IoT systems, it's essential to implement strong security measures to protect your data and devices. Here are some key considerations:
- Data Encryption: Use encryption protocols such as TLS or AES to secure data transmission.
- Firewall Configuration: Set up firewalls to block unauthorized access to your devices.
- Regular Updates: Keep your software and firmware up to date to patch known vulnerabilities.
For Raspberry Pi users, securing your device involves configuring SSH, enabling firewall rules, and using strong passwords. Additionally, consider implementing two-factor authentication (2FA) for added security.
Setup Process for Remote IoT P2P
Step 1: Install Required Software
Before you can securely connect your Raspberry Pi to remote IoT devices, you'll need to install the necessary software. This includes:
- Raspberry Pi OS
- SSH client
- P2P software (e.g., WebRTC, libp2p)
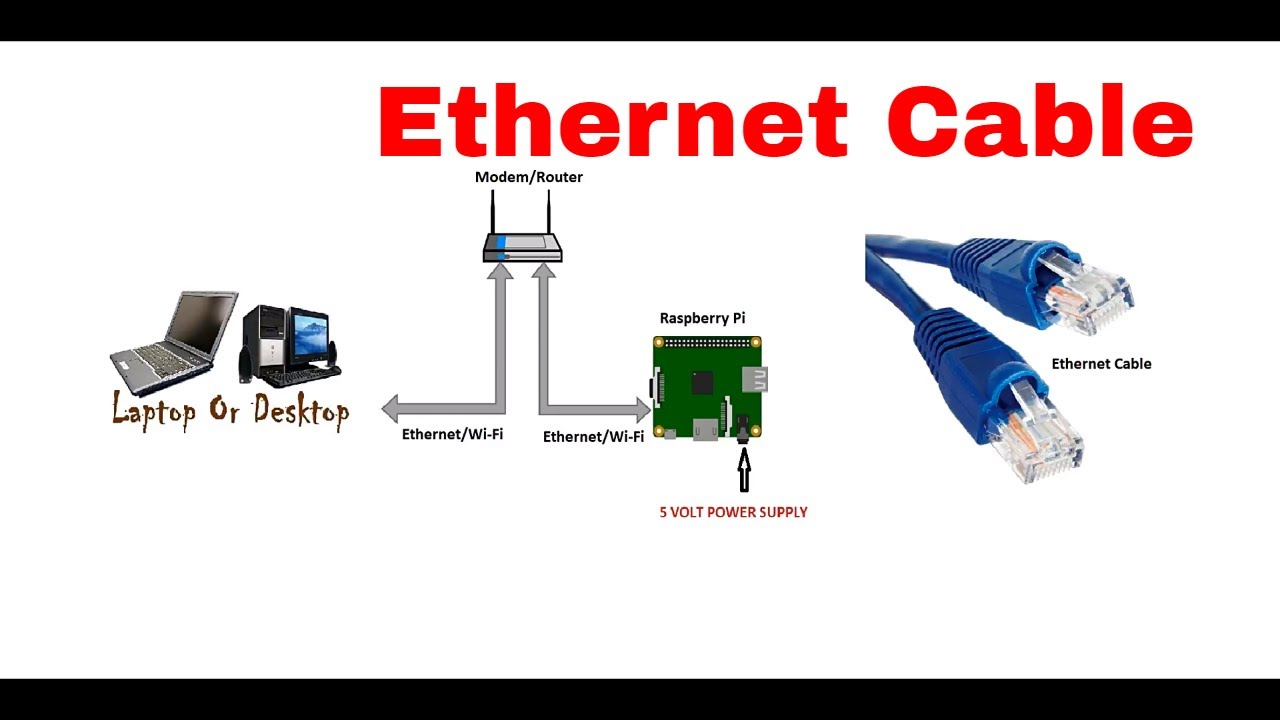
For Mac users, you can download the Raspberry Pi Imager from the official Raspberry Pi website to install the OS on your SD card. Once installed, connect your Raspberry Pi to your Mac using an Ethernet cable or Wi-Fi.
Step 2: Configure Raspberry Pi
Configuring your Raspberry Pi involves setting up SSH, enabling P2P functionality, and configuring network settings. Here's how you can do it:
- Enable SSH by creating an empty file named "ssh" on the boot partition of your SD card.
- Install P2P software using the package manager (e.g., apt-get).
- Configure network settings to allow communication with remote devices.
Once configured, your Raspberry Pi will be ready to connect to remote IoT devices using P2P technology.
Step 3: Secure the Connection
Securing your P2P connection involves implementing encryption, authentication, and firewall rules. Here are some steps you can take:
- Use SSL/TLS for encrypted communication.
- Implement strong authentication mechanisms, such as public key infrastructure (PKI).
- Set up firewall rules to block unauthorized access.
By following these steps, you'll ensure that your Raspberry Pi can securely communicate with remote IoT devices.
Mac-Specific Instructions
For Mac users, setting up a Raspberry Pi for remote IoT P2P connections involves a few additional steps. Here's a quick guide:
- Download the Raspberry Pi Imager from the official website.
- Use the Imager to install the Raspberry Pi OS on an SD card.
- Connect your Raspberry Pi to your Mac using an Ethernet cable or Wi-Fi.
- Use the Terminal app on your Mac to configure SSH and other settings.
By following these instructions, Mac users can easily set up their Raspberry Pi for secure IoT connectivity.
Common Issues and Troubleshooting
Even with careful setup, issues can arise when configuring a Raspberry Pi for remote IoT P2P connections. Here are some common problems and their solutions:
- SSH Connection Issues: Ensure that SSH is enabled and that your network settings are correct.
- P2P Configuration Problems: Verify that the P2P software is installed correctly and that network settings allow for peer-to-peer communication.
- Security Alerts: Check your firewall rules and ensure that all security measures are properly configured.
If you encounter any issues, consult the official Raspberry Pi documentation or seek help from online forums and communities.
Tips for Optimizing Performance
Optimizing the performance of your Raspberry Pi for remote IoT P2P connections can significantly improve its efficiency. Here are some tips:
- Use lightweight software and avoid unnecessary processes.
- Optimize network settings for low latency and high bandwidth.
- Regularly update your software and firmware to take advantage of performance improvements.
By following these tips, you'll ensure that your Raspberry Pi operates at peak performance, providing a seamless experience for your IoT applications.
Best Practices for Secure IoT Deployment
Deploying a secure IoT system requires adherence to best practices. Here are some recommendations:
- Use strong encryption protocols for all data transmissions.
- Implement multi-factor authentication for added security.
- Regularly monitor your devices for suspicious activity and update security measures as needed.
By following these best practices, you'll ensure that your IoT deployment remains secure and reliable.
Future Trends in IoT Security
As IoT technology continues to evolve, so do the security challenges and solutions. Some emerging trends in IoT security include:
- Blockchain Technology: Using blockchain to secure IoT data and transactions.
- AI-Powered Security: Leveraging artificial intelligence to detect and respond to threats in real-time.
- Quantum Encryption: Exploring the potential of quantum computing to enhance encryption protocols.
By staying informed about these trends, you'll be better prepared to secure your IoT systems in the future.
Conclusion
Securing remote IoT devices using P2P technology on a Raspberry Pi is a critical skill for anyone working with IoT systems. By following the steps outlined in this guide, you'll be able to set up a secure and efficient connection for your devices, ensuring that your data remains protected and your applications function optimally.
We encourage you to share this article with others who may benefit from it and to leave a comment below with any questions or feedback. Additionally, explore our other articles on IoT security and Raspberry Pi projects for more valuable insights.